 Scammers are something that I have been watching for a long time. This is affected me personally with my mother, that was scammed years ago. See “Police warn ‘Jamaican lottery’ scam preys on the elderly.” When I say Scammers, I mean anybody using technology to take advantage of someone.
Scammers are something that I have been watching for a long time. This is affected me personally with my mother, that was scammed years ago. See “Police warn ‘Jamaican lottery’ scam preys on the elderly.” When I say Scammers, I mean anybody using technology to take advantage of someone.
In this series of posts, I will break it all down starting from a consumer perspective on how people get scammed.
What does the scammer do simply?
They often make false promises, such as opportunities to buy products, invest your money, or receive free product trials. They may also offer you money through free grants and lotteries. Some scammers may call with threats of jail or lawsuits if you don’t pay them. Or just impersonate a famous person to gain trust and eventually your money.
Scams come in many forms and factors, but most of them are in trying to take advantage of our honesty. Text messages or any messaging app we use like these are quick to grab our attention. Studies show that the majority of incoming messages are opened within 15 minutes of receipt. Scammers know this and sometimes target consumers with “phishing” scams via text messages or another messaging service.
Smishing
Text message or SMS phishing—also called “smishing”—occurs when scammers use deceptive text messages to lure consumers into providing their personal or financial information. The scammers that send smishing messages often impersonate a government agency, bank, or other company to lend legitimacy to their claims. Smishing messages typically ask consumers to provide usernames and passwords, credit and debit card numbers, PINs, or other sensitive information that scammers can use to commit fraud. It can happen like this:
“John” received a text message that appeared to be from his local credit union. The message stated that his debit card had been deactivated. The message instructed him to call a toll-free telephone number, which he did. When John received a recording that asked him to enter his debit card and PIN, he hung up. He then called his credit union and spoke to a representative who stated his debit card was working properly and the text message was a scam.
“Catherine” received a text message from a local telephone number that stated she could receive a free $1,000 shopping spree at a big discount store if she were one of the first 100 visitors to a website linked to the message. Catherine immediately opened the link and was asked to enter her email address and credit card number. Catherine noticed that the website had the same color scheme and a similar font as the store’s website, but the store’s name was spelled incorrectly, and the URL did not start with “https://” like a secure website usually does. Catherine closed the link without providing any information and called her cell phone company to report the text message as a scam.
Social Media Scams
Scam #1: Social media phishing
Scammers create fake social media posts and profiles to convince you to share your personal or financial information. The profile may use a real company’s name or logo and often links to a fake website where you’re asked to enter your checking account or credit card number, SSN, or other sensitive information.
Common ploys include:
- Requests to report vaccine side effects
- Offers to receive grants or government benefits
- Deep discounts on expensive products
- Requests for charitable donations
If you provide your information to the scammer, it can be used to access your bank account, make fraudulent purchases, or steal your identity.
Other social media phishing tactics are quizzes that lure victims with clever questions such as “Which celebrity do you look like?” Launching a quiz app may unknowingly give a third-party access to your profile data that could be used to hijack your social media account or install malware.
Scam #2: Hacked profiles with requests for money
Instead of creating a fake profile, scammers may take over an existing one. This can happen when a scammer steals a username and password through a data breach, phishing, or malware. Scammers use the hacked profile to contact the person’s friends and family, ask for money, or promote a link to a fraudulent site they own.
Scam #3: Online dating
Scammers create fake social media profiles and use the promise of love to trick naive victims into sending them money. They may use a fictional name or falsely assume the identities of aid workers, military personnel, or professionals working abroad.
Once they gain your trust, they may claim to need funds for an emergency or other hardship and convince you to share your account information or send money before disappearing.
Some telltale signs of this scam include poor or vague communication, flowery language, a small number of Facebook or Instagram pictures and posts, or a Twitter account with just a few tweets.
Scam #4: Card cracking and job scams
In card cracking schemes, scammers use social media to post opportunities to make “easy money” in a way they say is “legit.” They typically request your debit card, PIN, and/or mobile banking username and password to deposit a fake check into your account. They may ask you to report your card lost or stolen or that your username and password have been compromised in order to seek reimbursement from your bank. In exchange, scammers promise you a portion of the money you deposit.
After gaining access to your account, scammers can transfer money or deposit phony checks and quickly make withdrawals before your bank identifies the bad checks. Not only are you robbed of your money, but you may also face hefty fines and criminal charges because your participation in this scheme makes you a co-conspirator.
In job scams, victims are promised a high-paying job in return for a small “advance fee” to secure a position that doesn’t actually exist. The phony employer may also send a new employee a fake check before their start date and require them to send back some money to pay for training or supplies. If the employee deposits the fake check, they will be responsible for the check amount and any money sent to the scammer.
Pull the plug on social media scammers with Do’s and Don’ts
Proof of social media’s explosive popularity is in the numbers. In 2021, 82% of the US population had a social networking profile.
A growing number of U.S. consumers are getting scammed on social media, according to a new report by the Federal Trade Commission (FTC), which revealed that consumers lost $770 million to social media scams in 2021 — a figure that accounted for about one-fourth of all fraud losses for the year.
- Do set your profiles to private and restrict your social media contacts to people you know personally.
- Do be on the lookout for suspicious posts, including limited-time offers, discounts that seem too good to be true, and requests for personal or account information.
- Do be wary of individuals you meet through social media sites, especially if they promise romance before you’ve met in person.
- Do create a unique username and password for each app and website you use to help protect against unauthorized access across multiple accounts.
- Don’t accept friend requests from strangers.
- Don’t respond to online solicitations for “easy money” and be wary of requests to send money back to an employer.
- Don’t click on suspicious links, even in posts from people you know – their accounts may have been hacked.
- Don’t fill out every field on your social media profile, such as your phone number and home address – including these details increases the chance of identity theft should you be hacked.
- Don’t send money to someone you have only met online. If you receive a request from a friend or family member for money, always contact them using a different method to make sure their profile was not hacked.
- Government agencies, banks, and other legitimate companies never ask via text message for personal or financial information, like usernames, passwords, PINs, or credit or debit card numbers.
- Don’t be rushed. Smishing scams attempt to create a false sense of urgency by implying that an immediate response is required or that there is a limited time to respond.
- Don’t “click” open links in unsolicited text messages. Clicking the link may infect your mobile device with a virus or malware designed to steal the personal or financial information stored on the device.
- Don’t call a telephone number listed in an unsolicited text message. To hide their identity, scammers often use email-to-text technology, shortcodes, or spoofed local numbers. You should contact any bank, government, agency, or company identified in the text message using the information listed in your records.
- Don’t respond to smishing messages; even to ask the sender to stop contacting you. Responding to smishing messages verifies that your phone number is active and that you are willing to open such messages, which may increase your unsolicited text messages.
- Use caution when providing your cell phone number or other information in response to pop-up advertisements and “free trial” offers. This personal information can be easily bought, sold, and traded, making you a target for smishing scams.
- Never provide your personal or financial information in response to text messages from unknown senders. Verify the identity of the sender and take the time to ask yourself why the sender is asking for your information.
- Use the same safety and security practices on your cell phone as you do on your computer: be cautious of text messages from unknown senders and unusual text messages from senders you know, and keep your security software and applications up to date.
My next post will investigate one particular case I was involved in, and I will detail how the person was scammed and what we did to stop them and end it.
Until next time,
Rob




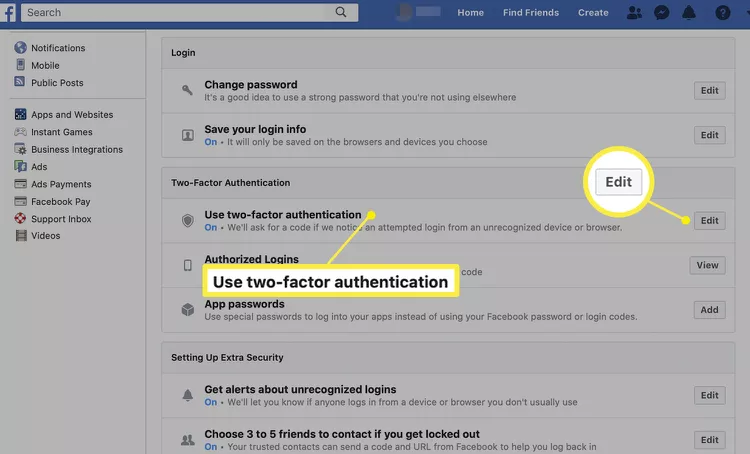
 In an age where cyber threats are an unfortunate part of daily digital life, protecting your online accounts is paramount. I get asked or hear about a relative/friend getting hacked because of just having a simple or easily crackable password. One of the most effective ways to bolster your online security is through Multi-Factor Authentication (MFA), often referred to as Two-Factor Authentication (2FA). In this post, we’ll dive into the importance of MFA and guide you on activating it on popular social media platforms: LinkedIn and Facebook.
In an age where cyber threats are an unfortunate part of daily digital life, protecting your online accounts is paramount. I get asked or hear about a relative/friend getting hacked because of just having a simple or easily crackable password. One of the most effective ways to bolster your online security is through Multi-Factor Authentication (MFA), often referred to as Two-Factor Authentication (2FA). In this post, we’ll dive into the importance of MFA and guide you on activating it on popular social media platforms: LinkedIn and Facebook.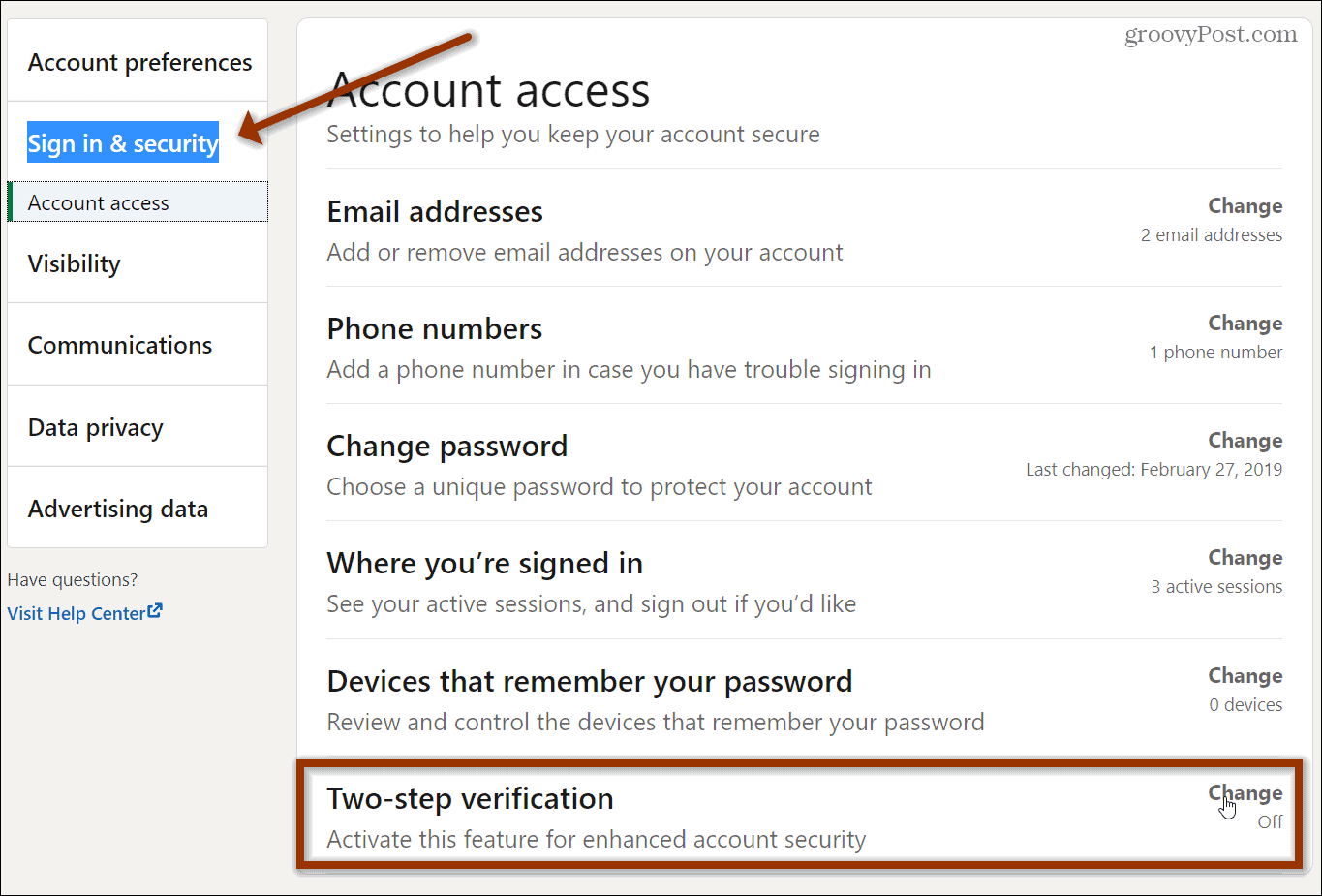
 TikTok, a social media platform owned by ByteDance, a Beijing-based company, has taken the world by storm. Its short-form video content has attracted millions of users, particularly among the younger generation. However, as with any technology, it comes with its own set of risks and concerns. This blog post will delve into the technical dangers associated with TikTok, including data privacy, censorship, and potential misuse of the platform.
TikTok, a social media platform owned by ByteDance, a Beijing-based company, has taken the world by storm. Its short-form video content has attracted millions of users, particularly among the younger generation. However, as with any technology, it comes with its own set of risks and concerns. This blog post will delve into the technical dangers associated with TikTok, including data privacy, censorship, and potential misuse of the platform. In today’s digital world, protecting an organization’s information and assets from cyber threats has never been more critical. The rise in cyber attacks and security breaches has made it crucial for organizations to have a centralized platform to manage their security operations and respond to incidents promptly and effectively. That’s where Azure Sentinel comes in.
In today’s digital world, protecting an organization’s information and assets from cyber threats has never been more critical. The rise in cyber attacks and security breaches has made it crucial for organizations to have a centralized platform to manage their security operations and respond to incidents promptly and effectively. That’s where Azure Sentinel comes in.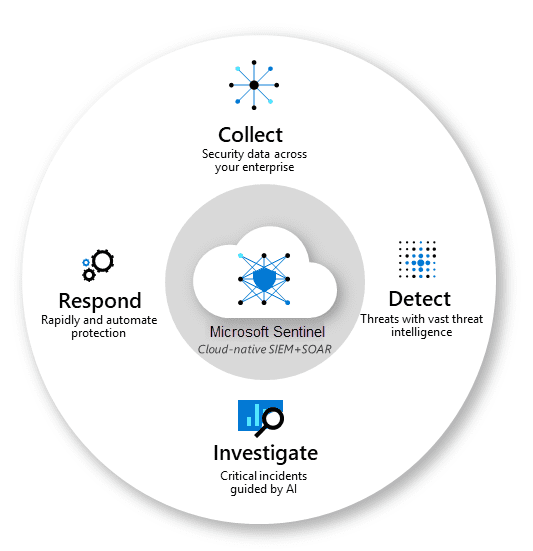
 Scammers are something that I have been watching for a long time. This is affected me personally with my mother, that was scammed years ago.
Scammers are something that I have been watching for a long time. This is affected me personally with my mother, that was scammed years ago. 